A user on the XSS forum made a post about the newly developed stealer and publicly opened beta testing of the product. Below is the machine translation of forum post. The machine translation is done by using DeepL.com, and some minor edits by me. All the screenshots are taken from the XSS forum.
TheVoid – Open Beta Test {STEALER}
Hello everyone! Lately the market of most forums has been flooded with stealers. Over time, I have used almost every project on the market, but I found a number of drawbacks in each of them, sometimes insignificant, but still drawbacks. Eventually, I came to the conclusion that creating my own project was no longer a dream, but a perfectly reasonable idea.
At this point, I am announcing the beta testing of my project. Anyone can access the project absolutely free of charge. Let’s take a quick look at the project itself:
C/C++ Build x64 was used to write the build. Weight 550-600kb CRT static. To interact with the system, we use different interaction methods. To work with files and process memory, we used direct calls to system calls, and I dynamically obtain the system call numbers from memory, which eliminates the need to open the necessary DLLs. For other tasks, standard NtAPI / WinAPI are used.
Build collects data from about 20 browsers (Chrome, Edge, Brave, Opera, Firefox, etc.). All decryption is done on the server side; databases are not opened on the victim’s side. A configuration system has been implemented that allows you to add the browser/extension or even wallet you need in just a couple of clicks.
Of course, a collection of standard software (Steam, Discord, Telegram, Filezilla, etc.) is implemented.
We also have a fairly advanced graber, in whose configuration you can set the depth of recursive search, target names/extensions, and maximum file size. When sending the found files, their hash is collected in a table and blocks the sending of duplicates.
Absolutely every request from the client to the build goes in a separate request, which allows you to store part of the data on the server even if the build crashes at runtime. The connection is established via HTTPS and is additionally covered by XOR encryption.
In our proxy system, we have calculated the minimum trigger for antivirus programs and corporate bots. A proxy is not just NGINX translating data to the main server; it is a full-fledged separate server that accepts data. If for some reason the main server goes down, your traffic will not be lost, and all data will be stored in raw form on the proxy and will wait for the main server to be turned on for processing.
Main panel:
Due to recent events in the world (arrests and takedowns of servers, creators, projects), I decided to create a safe space for users. The main panel is located in the TOR network, and we do not store any customer data (cryptocurrency addresses, contact information, IP addresses, user agents, etc.).
The panel is written in Rust, which was chosen for maximum performance.
It has standard stealer functionality:
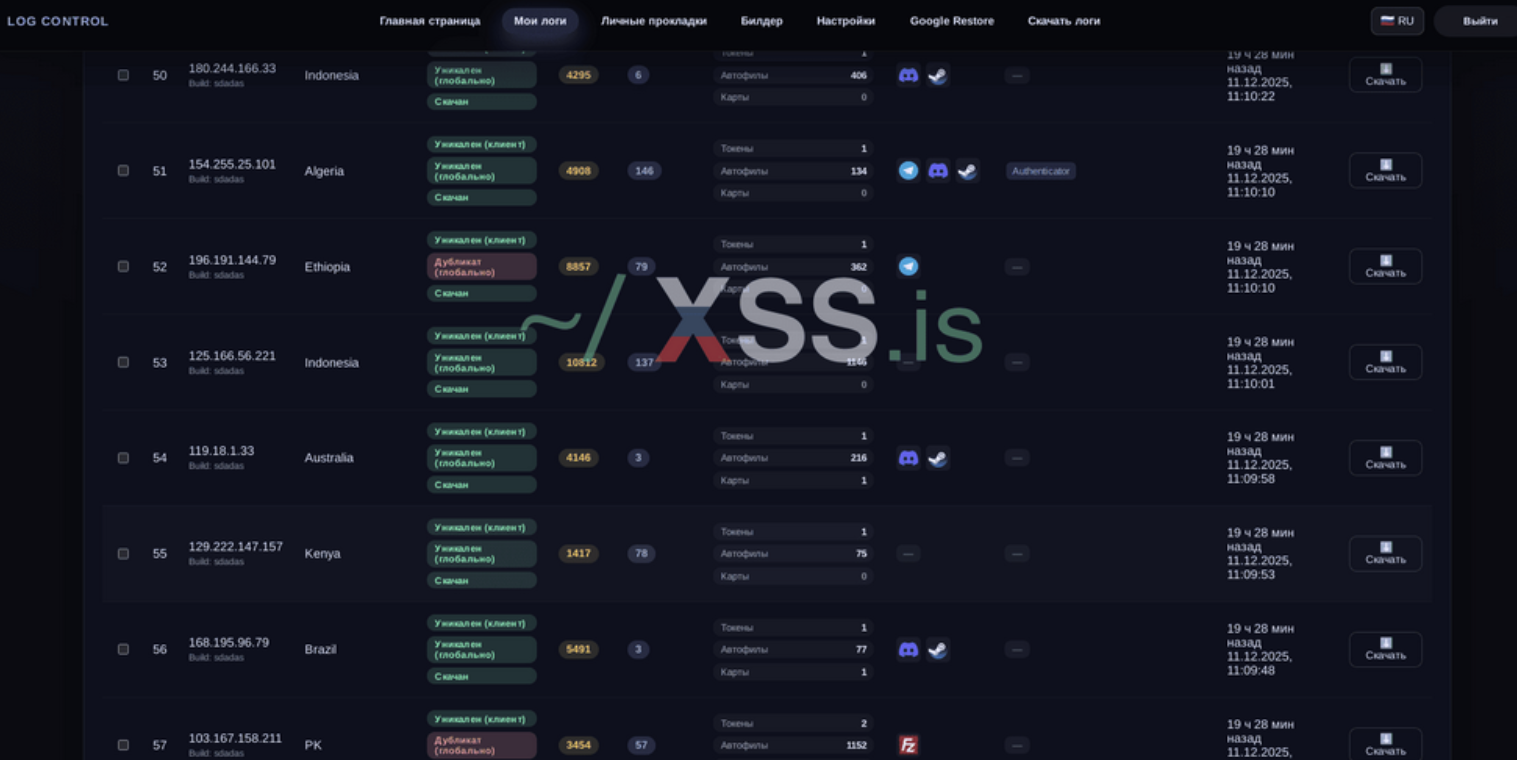
Statistics
Table + Log search
Builder
Ability to create personal proxies
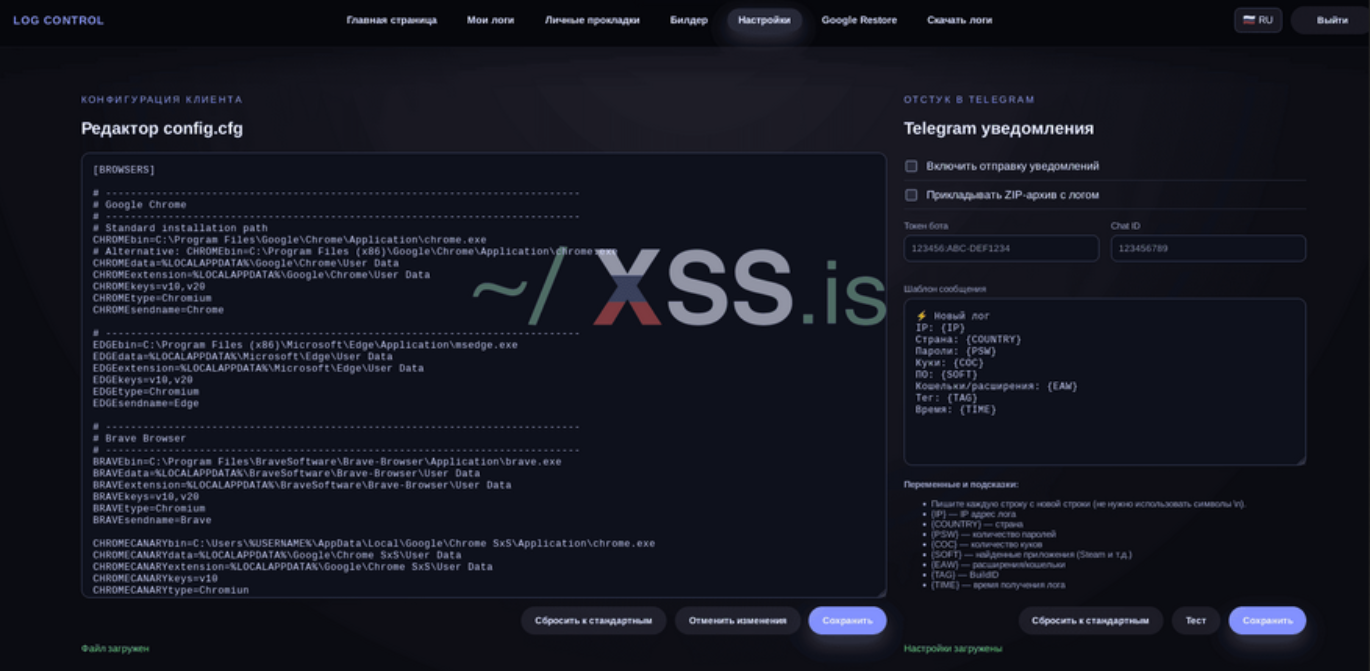
Settings (config + TG delivery)
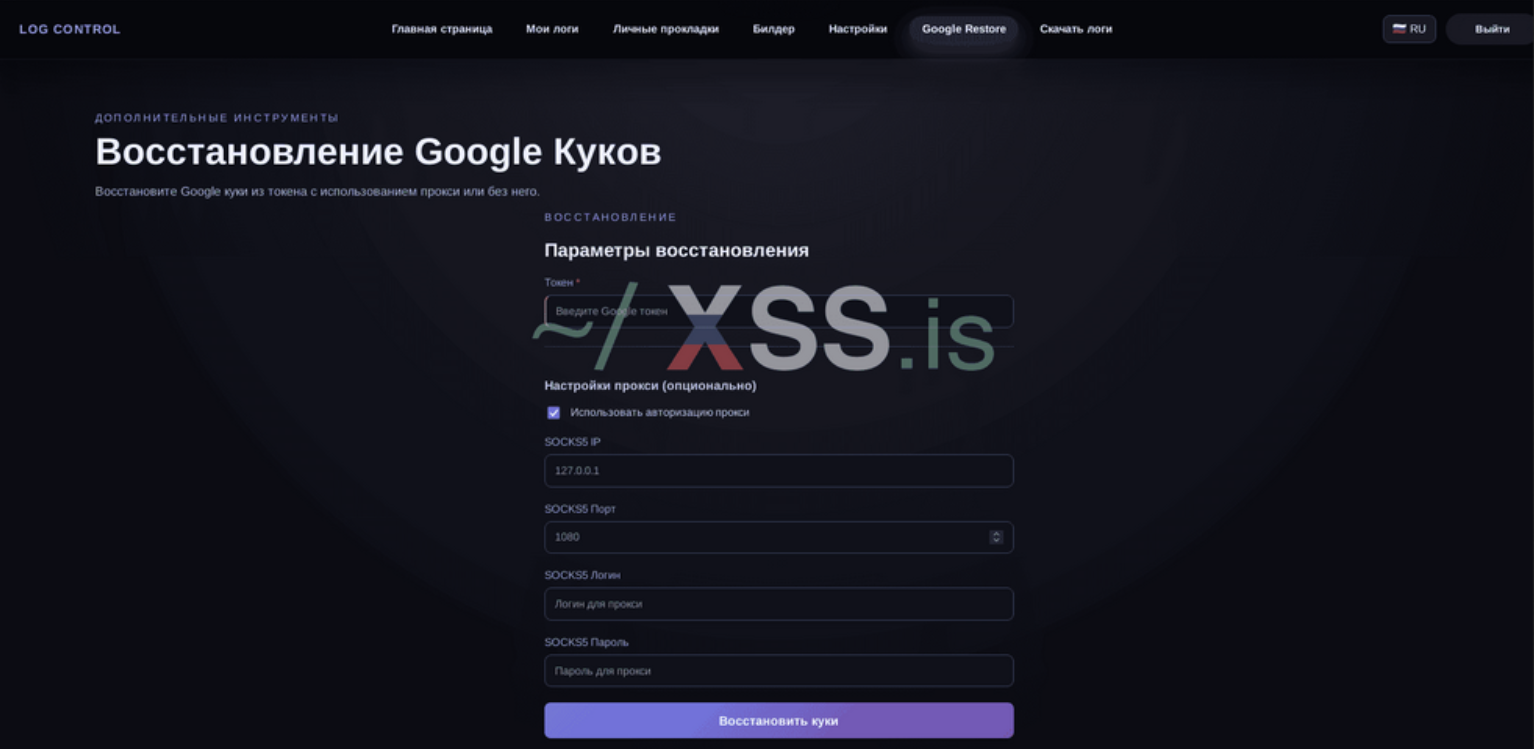
Google Restore
Log download page
You can see screenshots of the panel at the bottom of the topic.
The stealer was tested extensively (installs, users in RAT) before the start of this event, but we want to see how it will perform in real combat conditions.