A brief look at all things infostealers for the week 38, 2025 (15.09.2025–21.09.2025). There were few updates in infostealers, and I registered on a few more forums. On the WWH Club forum I discovered that Lumma and Vidar stealers made updates after a long hibernation. In addition, a new update from AURA stealer spotted on XSS forum. Grabbed some numbers from marketplaces and some interesting news/articles.
Note: The update posts are copy-pasted as is (and machine-translated with DeepL.com if post wasn’t available in English, possibly with some minor edits by me).
Infostealer Updates
AURA Stealer
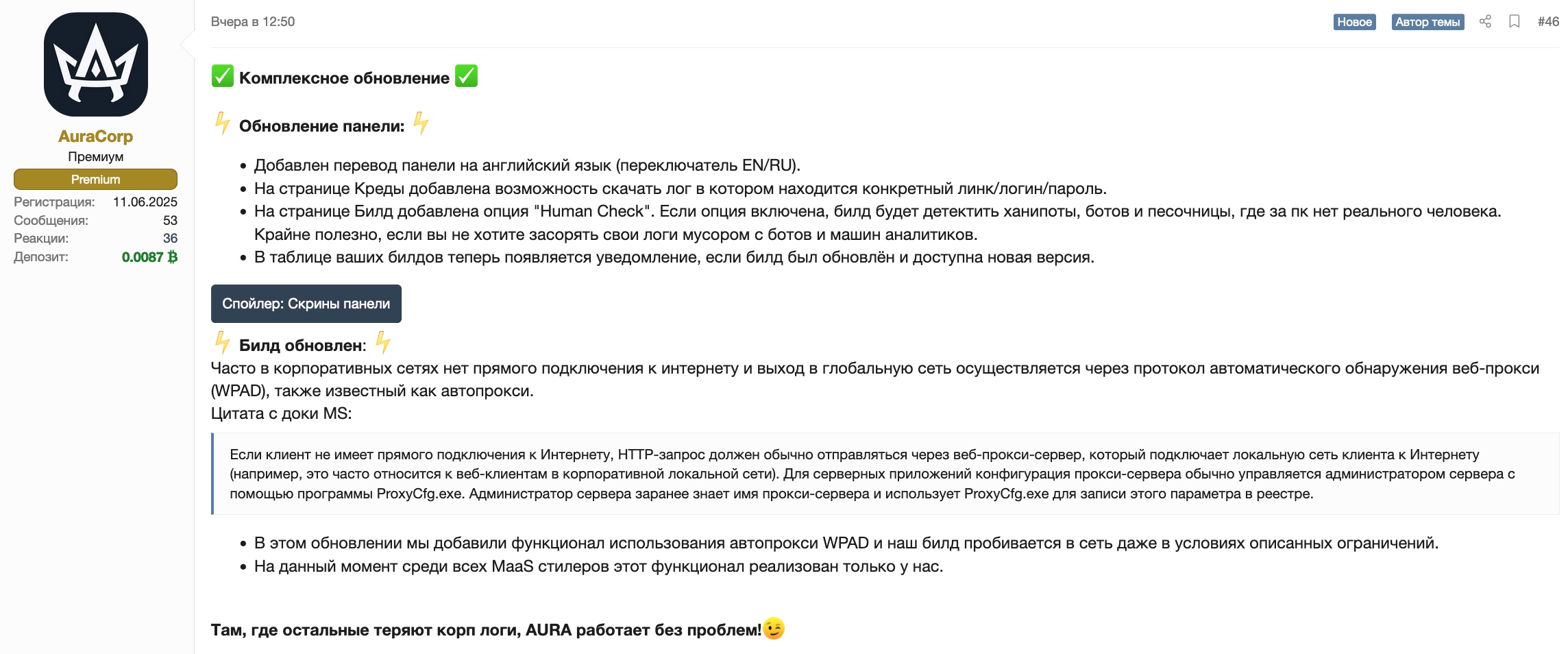
Comprehensive update
Panel update:
- Added English translation of the panel (EN/RU switch).
- Added the ability to download a log containing a specific link/login/password on the Credentials page.
- Added the “Human Check” option on the Build page. If this option is enabled, the build will detect honeypots, bots, and sandboxes where there is no real person behind the PC. This is extremely useful if you don’t want to clutter your logs with junk from bots and analytics machines.
- A notification now appears in your builds table if the build has been updated and a new version is available.
Build updated:
Corporate networks often do not have a direct connection to the Internet, and access to the global network is provided via the Web Proxy Auto-Discovery Protocol (WPAD), also known as autoproxy.
Quote from MS documentation:If the client does not have a direct connection to the Internet, the HTTP request must usually be sent through a web proxy server that connects the client's local network to the Internet (for example, this often applies to web clients on a corporate local network). For server applications, the proxy server configuration is usually managed by the server administrator using the ProxyCfg.exe program. The server administrator knows the name of the proxy server in advance and uses ProxyCfg.exe to write this setting to the registry.
- In this update, we added the functionality of using WPAD auto-proxy, and our build breaks through to the network even under the conditions described above.
- At the moment, among all MaaS stealers, this functionality is only implemented by us.
Screenshot from XSS forum
VIDAR Stealer
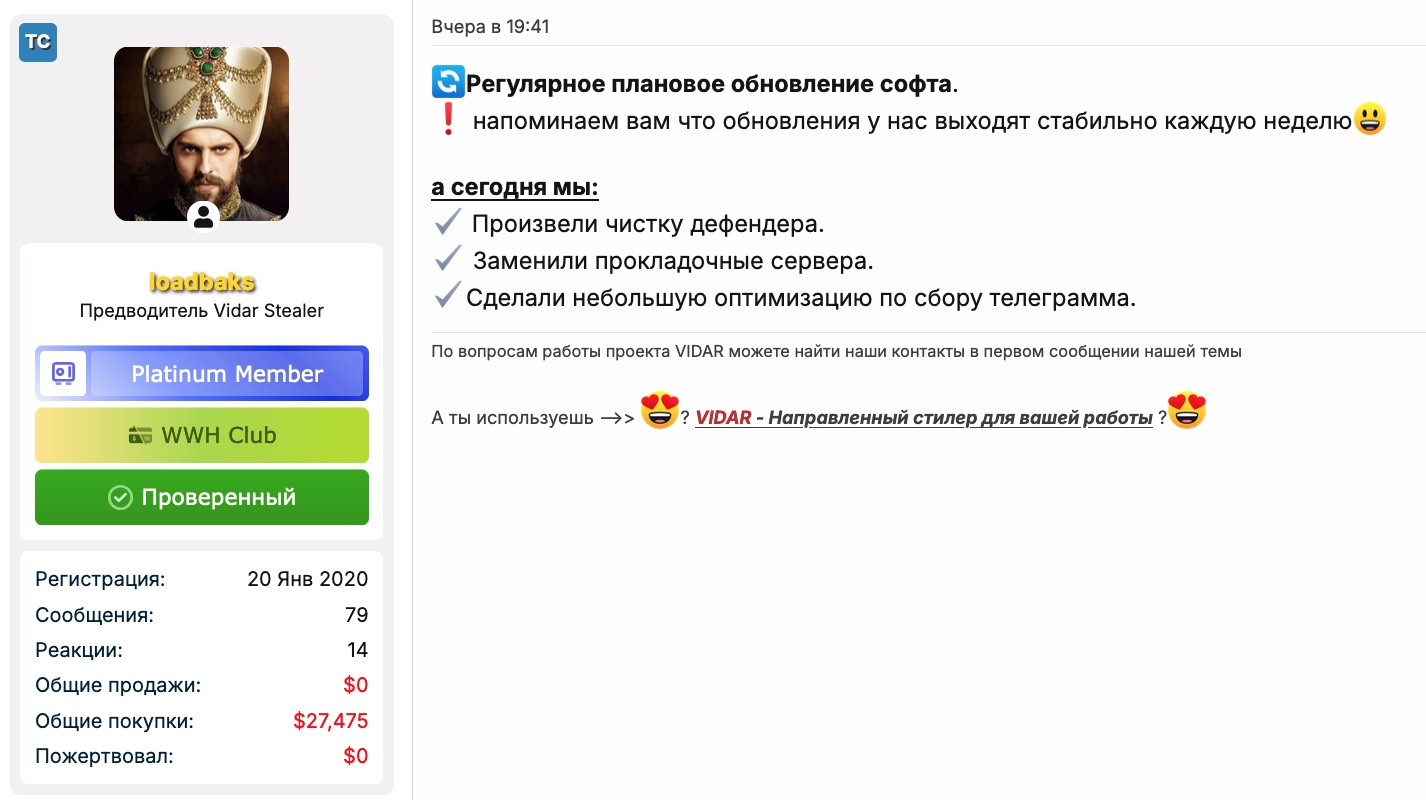
Regular scheduled software updates.
We would like to remind you that we release updates every week.
Today, we:
- Cleaned up the defender.
- Replaced the proxy servers.
- Made minor optimizations to Telegram collection.
Screenshot from WWH Club forum
LummaC2 Stealer
Update 27.08
- Cleaned WD 10/11 + Cloud
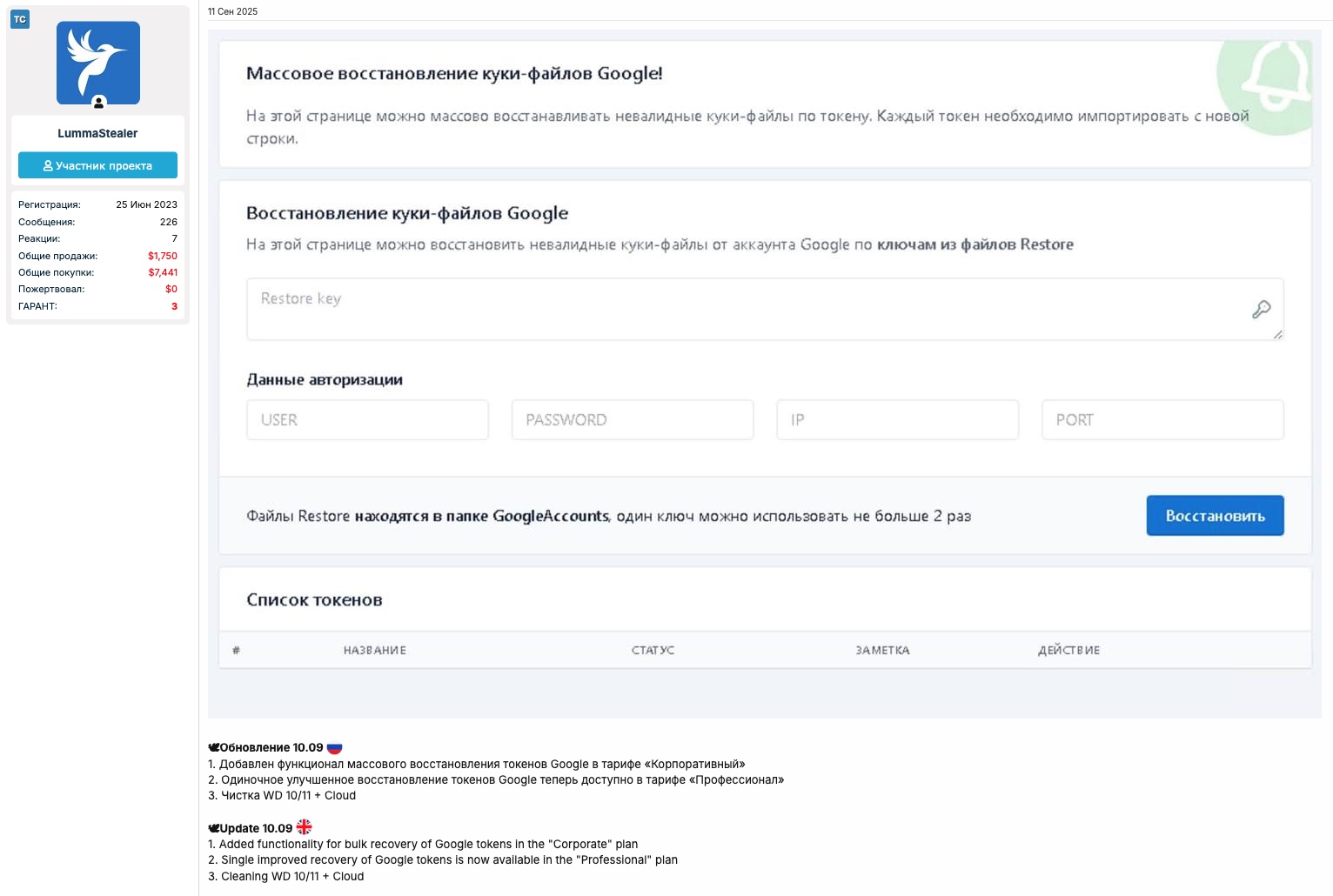
Update 10.09
- Added functionality for bulk recovery of Google tokens in the “Corporate” plan
- Single improved recovery of Google tokens is now available in the “Professional” plan
- Cleaning WD 10/11 + Cloud
Screenshot from WWH Club forum
Marketplace Updates
This section provides some numbers taken from the marketplaces, which include numbers of victims based on stealers, top 5 countries, the victim numbers in the countries of the Nordic region. In addition, see the CryptPad spreadsheet for all more broad numbers.
Marketplace Updates Spreadsheet
Russian Market
Stealers by number of victims
| Stealer name | Number of victims |
|---|---|
| Lumma | 6,964,072 |
| Vidar | 547,452 |
| RisePro | 145,554 |
| StealC | 743,615 |
| RedLine | 192,193 |
| Acreed | 512,194 |
| Racoon | 5,091 |
| Rhadamanthys | 165,351 |
Top 5 countries by number of victims
| Country | Number of victims |
|---|---|
| India | 1,075,508 |
| Brazil | 677,149 |
| Indonesia | 525,265 |
| Egypt | 456,947 |
| Pakistan | 393,532 |
Nordic region countries
| Country | Number of victims |
|---|---|
| Sweden | 18,571 |
| Denmark | 10,184 |
| Norway | 8,220 |
| Finland | 6,605 |
| Iceland | 959 |
| Greenland | 138 |
| Faroe | 91 |
| Åland | 21 |
Exodus Market
Stealers by number of victims
| Stealer name | Number of victims |
|---|---|
| Lumma | 475,069 |
| Rhadamanthys | 107,507 |
| RedLine | 35,127 |
| StealC | 26,646 |
| Vidar | 11,548 |
Top 5 countries by number of victims
| Country | Number of victims |
|---|---|
| India | 71,751 |
| Brazil | 50,466 |
| Indonesia | 37,170 |
| USA | 28,938 |
| Philippines | 24,783 |
Nordic region countries
| Country | Number of victims |
|---|---|
| Sweden | 1,914 |
| Denmark | 1,052 |
| Norway | 825 |
| Finland | 611 |
| Iceland | 85 |
Articles/News
UNMASKING A PYTHON STEALER – “XillenStealer”
- https://www.cyfirma.com/research/unmasking-a-python-stealer-xillenstealer/
- https://www.pointwild.com/threat-intelligence/raven-stealer
- https://blog.lastpass.com/posts/attack-targeting-macs-via-github-pages
From ClickFix to MetaStealer: Dissecting Evolving Threat Actor Techniques
- https://www.bleepingcomputer.com/news/security/from-clickfix-to-metastealer-dissecting-evolving-threat-actor-techniques/
FileFix in the wild! New FileFix campaign goes beyond POC and leverages steganography
- https://www.acronis.com/en/tru/posts/filefix-in-the-wild-new-filefix-campaign-goes-beyond-poc-and-leverages-steganography/