A new infostealer MaaS, named AURAStealer, was advertised on the XSS forum. Below is the machine translation of forum post. The machine translation is done by using DeepL.com.
All the screenshots are taken from the XSS forum. I have skipped few screenshots of the MaaS’s panel due to them being nearly the same as other panel pages.
AURA Stealer is a carefully calibrated solution where every detail exists not for beauty, but for results.
Collection of more than 110 browsers, 70 applications, including wallets and 2FA, and more than 250 browser extensions. That’s not all, at any time you can add any app or extension to the collection config in a couple of clicks.
Collect cookies from open Chromium browsers without killing the process (no cookie bashing). Own shellcode for App-Bound decryption. All decryption is server-side – build does minimum suspicious actions.
Loader is present. The build weighs ~500-700 Kb and is enhanced with a morpher developed from scratch. This and much more is waiting for you with AURA!
About us:
Our team is experienced specialists with 5 to 11 years of experience.
Developers study new technologies every day and take our code to the next level. The guys have been creating cutting-edge solutions for years, and their attention to detail and commitment to perfection allow us to always be one step ahead.
System administrators ensure stable operation and protection of our services, identify and neutralize problems before they occur. The guys have extensive experience in maintaining complex systems and are ready for any challenge.
Testers maintain the high quality and reliability of our product by testing it at all stages of development.
Support will not leave you with a problem alone and will be happy to help with issues. We value your time and effort, so we strive to provide fast and quality assistance.
AURA team is a combination of talent, experience, a huge reserve of energy and interesting ideas.
All participants are united by one goal – to create and develop the best product of its kind, which will be said: “This is exactly what I was looking for!”.
Web:
At the entrance you will be greeted by a panel built using the popular and beautiful Tabler web template.
You will get an intuitive and pleasant interface that has already proven itself among many users. We believe that modern design and well thought-out structure of the panel will please you and create conditions for comfortable work.
A few facts:
- The panel is fast. Requests to the database pass the caching layer and happen almost instantly.
- Each user’s data is securely protected by strict access policies.
- To maintain the speed of the database, it is regularly optimized and cleaned.
- We use powerful servers, which ensures fast performance of our systems and high uptime.
- In our panel you can customize the color scheme, choose light or dark theme, fonts and much more to your taste.
Build:
- The build is written in C++ (NtAPI/WinAPI + CRT/STL). Build weight ~500-700 Kb (different in each build after morphing), compressed to 170-250Kb by packers.
- Statically linked, runs on Win7 – Win11. No dependencies, runs on clean systems.
- Parts of the code critical to speed or secrecy are built on NtAPI, less demanding – on WinAPI.
- Imports are hidden, functions are obtained dynamically and cached in an encrypted hash table. Function addresses are not stored in plaintext and are decrypted just before calling. Only CRT imports and fake imports (changed during rebuild) are present in the build.
- Strings are encrypted and decrypted in runtime.
- Protection against double start (dynamic mutex based on DGA principle).
- Customizable Sleep before startup.
- AntiVM/Sandbox. Standard virtual/emulated environment checks. Can be enabled or disabled in the panel.
- AntiDebug. Nasty anti-debugging methods tightly integrated with our technologies. They will make even hardcore reverse engineers spit in the monitor. AntiDebug cannot be disabled in the panel.
- ApiHammering. Background noise to simulate legitimate activity and randomize behavior in runtime. Random WinAPI calls and file system interactions (create, write, read files) irrelevant scattered throughout the code.
- Powerful grabber with flexible collection customization. In the panel you can set the initial collection path, search masks, recursion level, file size limit, archive folder and other parameters depending on the type of collection.
- Very fast and compact Wildcard engine for searching files by masks from the config. When others offer search only by file extensions, we allow you to build more complex rules with different nesting levels (like folder/folderabcdef/.txt). And also relative paths with exit from the initial directory to the level above (e.g. ../folder/*.txt), this is useful for collecting by process name when the initial collection folder is unknown.
- The grabber has built-in protection against duplicate collection – the paths of read files are cached in a hash table. In case of incorrect configuration settings, you will not receive a log with duplicate files.
- When the grabber is working, nothing is dropped to disk, archives are built in RAM. The log is transmitted to the server in parts, even if the build catches a runtime detection, part of the data will be already on the server and you will not lose the whole log.
- All traffic between build and C2 is encrypted with AES-256 and goes through HTTPS protocol (its own wrapper over WinHTTP).
- In case of connection loss, the build cyclically waits for an internet connection, then continues from where it left off. In case of problems with the pad, selects a random working one and continues sending.
- Protection against non-crypted file spilling. If the build is run without crypto, a window-captcha will appear. After entering the captcha, the build will work as normal. After crypt/packaging the captcha does not appear.
- Build does not knock in CIS countries (CIS / former USSR)! Checking the layout and language of the system + checking IP on the server.
Build is complemented by a powerful morpher (obfuscator). At the moment we have implemented the following functionality:
- String encryption
- Obfuscation of numeric constants
- Permutation
- Hiding references to global variables (access via encrypted pointers)
- Hiding function addresses (indirect calls via encrypted addresses)
- Hiding function arguments
- Garbage code generation
- False branching
- Indirect jumps (jmp via encrypted addresses)
- Control Flow Flattening
- Code virtualization
Panel functionality and screenshots:
Main Page:
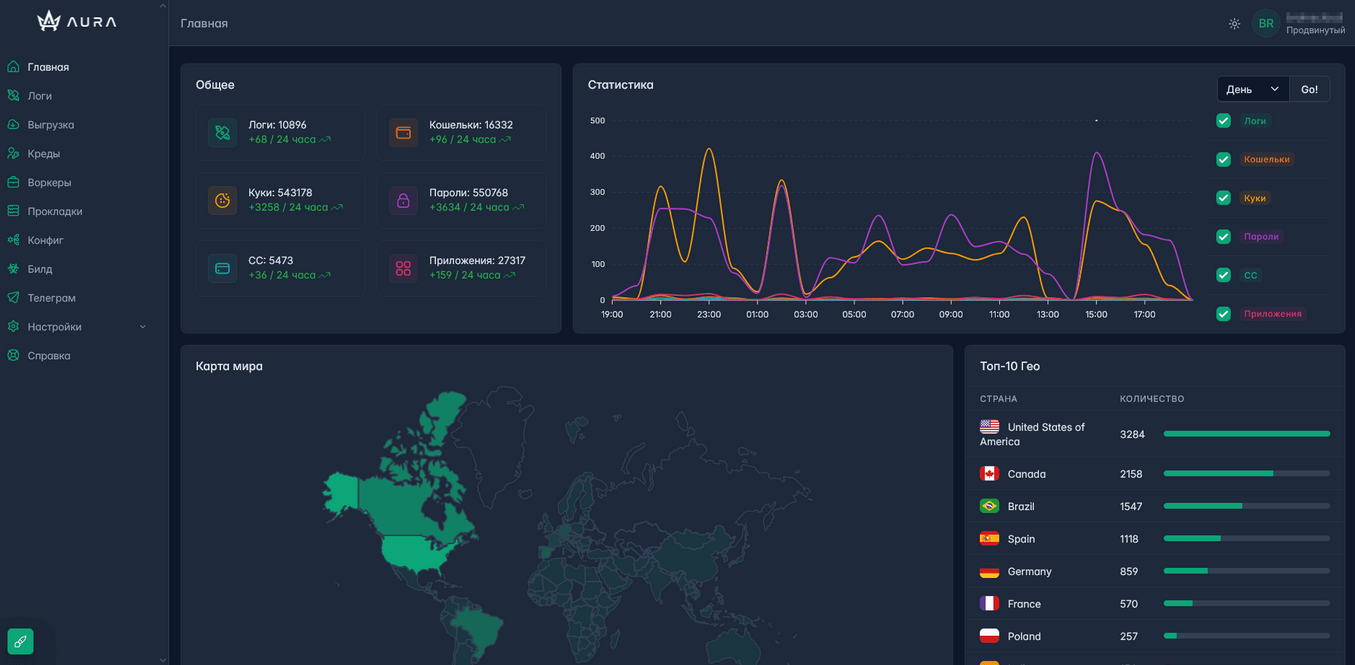
Here you can see the statistics of your work, informative graph (logs, wallets, cookies, passwords, cc and applications), world map with the scale of your work, as well as the list of top countries!
Main page
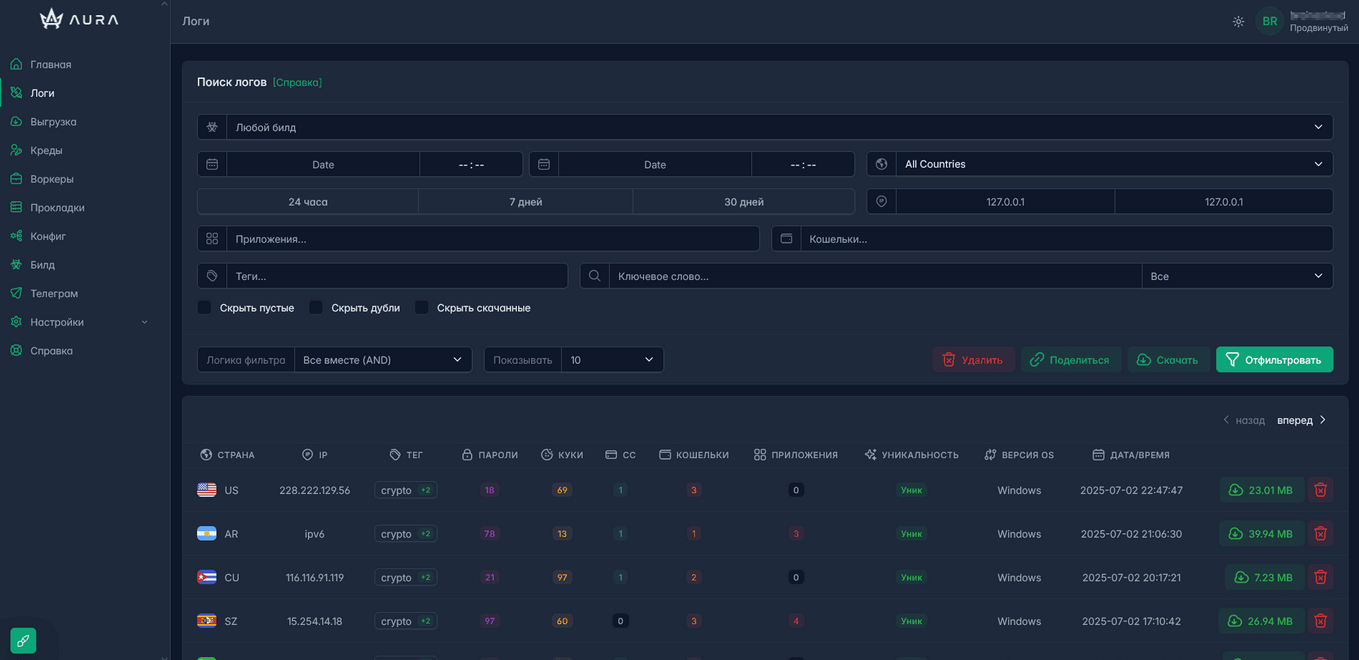
Logs:
On this page you can see:
- Convenient and flexible log filtering
- Select filtering type by single(s), multiple(s)
- Bulk extraction and deletion by filter
Logs
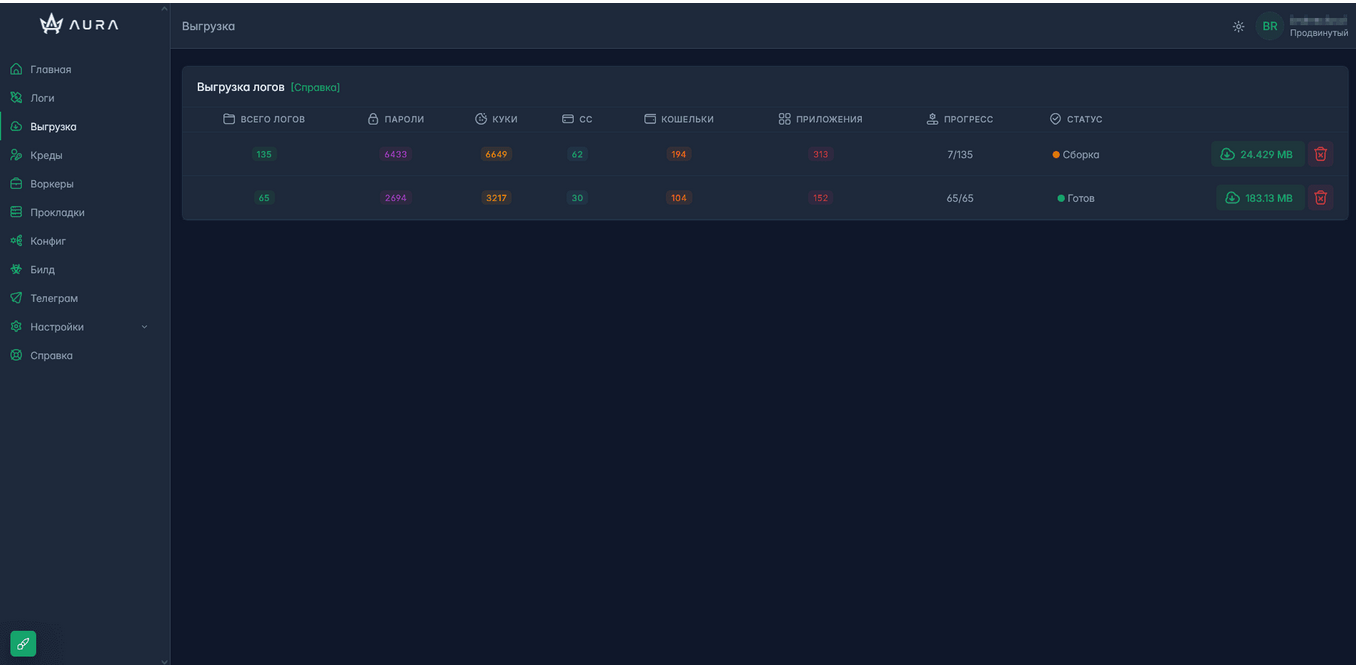
Extraction:
The page where logs are sent for bulk extraction.
Extraction
Credentials:
Search for credentials (links, logins, passwords) and download them.
Proxies:
Adding and removing personal ReverseProxy for build tapping.
Proxies
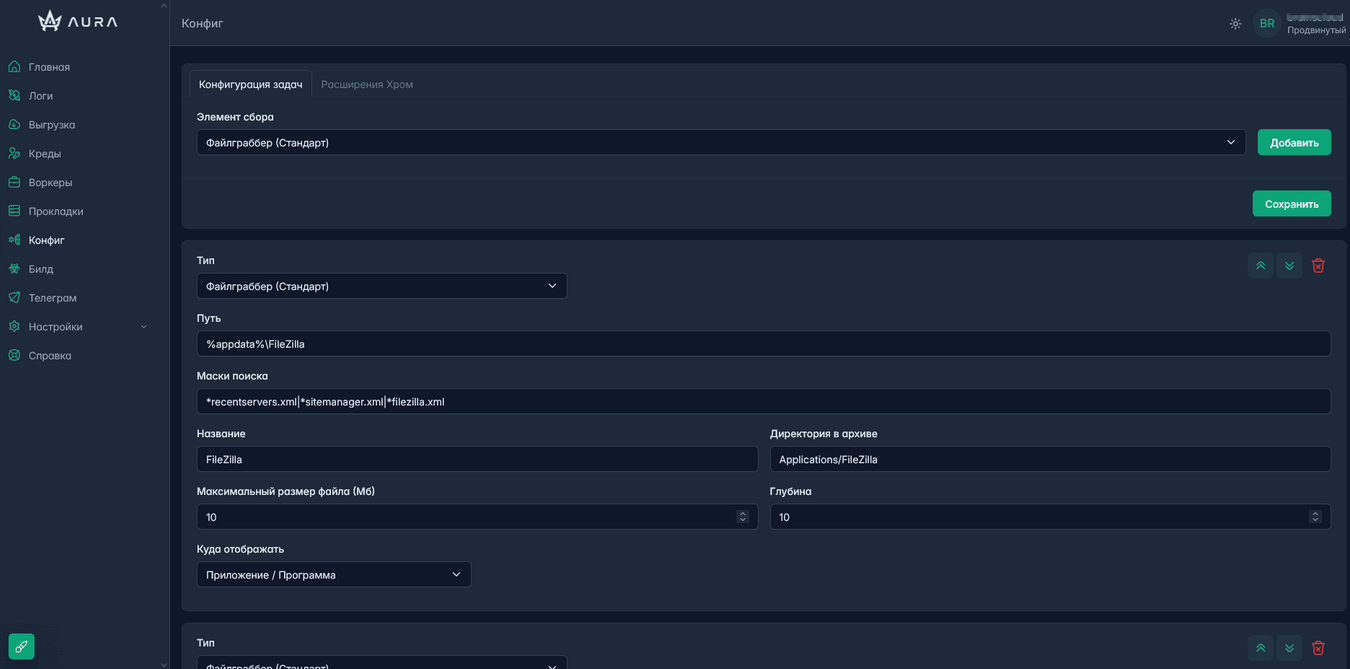
Config:
A well-customized standard grabber config is provided. In addition, it is possible to create and customize your own configs for any task.
The configs can be changed “on the fly” during a spill, and the build will pick up all changes on the fly. You can add the following collection options to the config:
- Filegrabber (Standard)
- Filegrabber (Process Name)
- Browser (Chromium)
- Browser (Gecko)
- Screenshot
- System Info
- Loader
- Reсent (Recent Files)
There is an additional tab for customizing Chrome extension collection.
The default configuration already has ~250 extensions added. You can expand this list in a couple of clicks.
Config
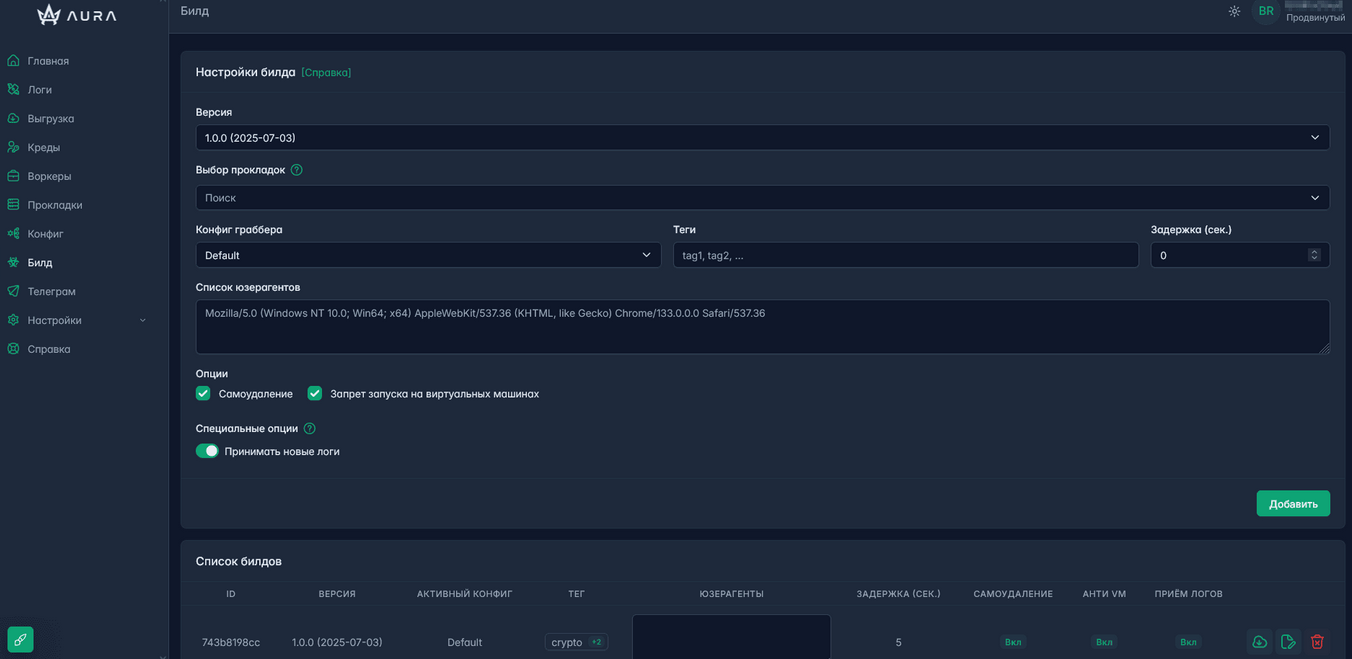
Build:
Easy customization of build:
- Ability to select build version
- Select Proxy(pads)
- Select config
- Add tags
- Set delay before start
- Additional options (Self-Removal, AntiVM)
Build
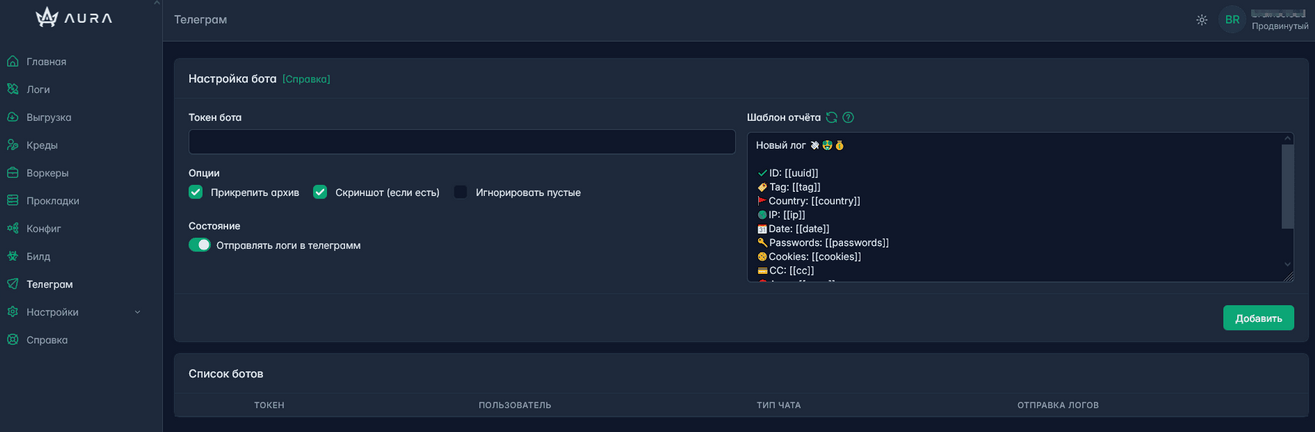
Telegram:
- A page for linking telegram bots
- Additional options: pin archive, add screenshot (if any), ignore empty ones
Telegram
Settings:
Subscription subsection
Subscription status and renewal.
Profile Subsection
- Change Password
- Set the timezone to display the date and time in the desired time zone.
Help:
Guide on operating the panel.
Help
Why choose us?
When creating AURA Stealer, our team’s goal was to eliminate competitors’ weaknesses and multiply their strengths.
We offer unique features and capabilities that will help you reach the next level and stand out in the market.
Our team is well aware that there is always something to strive for, so we are constantly improving our product to keep you one step ahead.
Our dashboard is intuitive and easy to use – you won’t need any special knowledge or skills to get started in it. You can always contact our support team for help or advice.
We offer flexible terms and conditions so you can choose the option that suits you best. Start with minimal investment and increase your income, surround yourself with the “AURA of Success” with us!
Pricing Rates
Basic ($295/month). Your path to success starts here!
- Search by keyword
- Search by country
- Search by date and time
- Ability to add 1 bulk upload to the queue
- Ability to customize collection of browser extensions
- Add 1 grabber config besides the standard one
- Ability to bind 1 tag to a build
- Create one build (customization template)
- Link one Telegram bot
Advanced (585$ / month). The golden mean for those who are used to winning!
- Advanced type of log filtering
- Ability to search by build
- There are buttons for quick date selection by filter (24h, 7d, 30d)
- Search by tags
- Search by applications
- Search by wallets
- Search by IP address and ranges
- Additional options (hide empty, hide duplicates, hide downloaded)
- Limit of mass uploads increased to three
- Possibility to create up to 5 links for Workers
- Possibility to add 3 additional configs besides the standard one
- Possibility to bind up to 5 tags to a build
- Add a list of user agents in a build (used for sniffing)
- Disable new logs on a specific build
- Possibility to create up to 5 builds (customization templates)
- Possibility to link up to 5 telegram bots.
Team:
The tariff is under development.
In the near future we will please you and your team with something interesting!
Stop reading – it’s time to act!