A brief look at all things infostealers for the week 23, 2025 (02.06.2025–08.06.2025). This week observed updates in MonsterV2 and Mac.c macOS stealers. Grabbed some numbers from marketplaces and some interesting news/articles.
Infostealer Updates
MonsterV2
Note: The update posts are copy-pasted as is (and machine-translated if post wasn’t available in English, possibly with some minor edits by me)
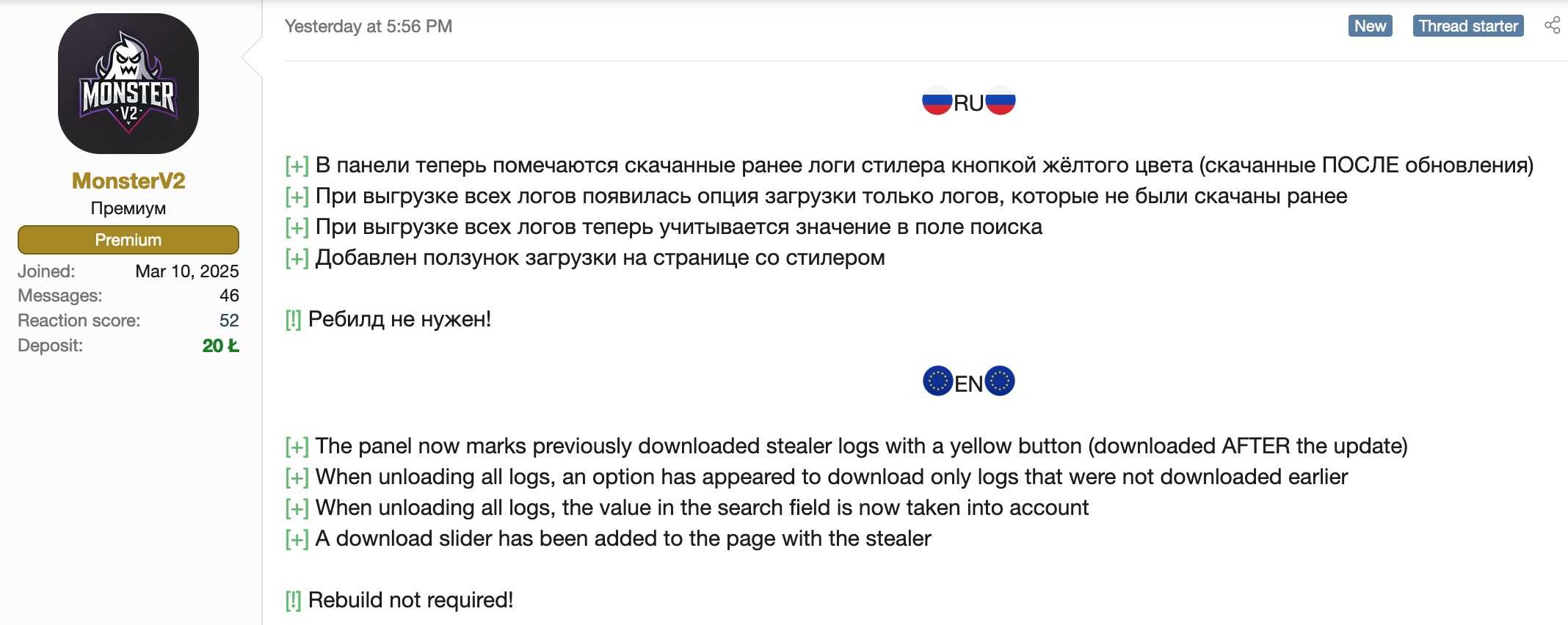
[+] The panel now marks previously downloaded stealer logs with a yellow button (downloaded AFTER the update)
[+] When unloading all logs, an option has appeared to download only logs that were not downloaded earlier
[+] When unloading all logs, the value in the search field is now taken into account
[+] A download slider has been added to the page with the stealer
[!] Rebuild not required!
Screenshot from XSS forum
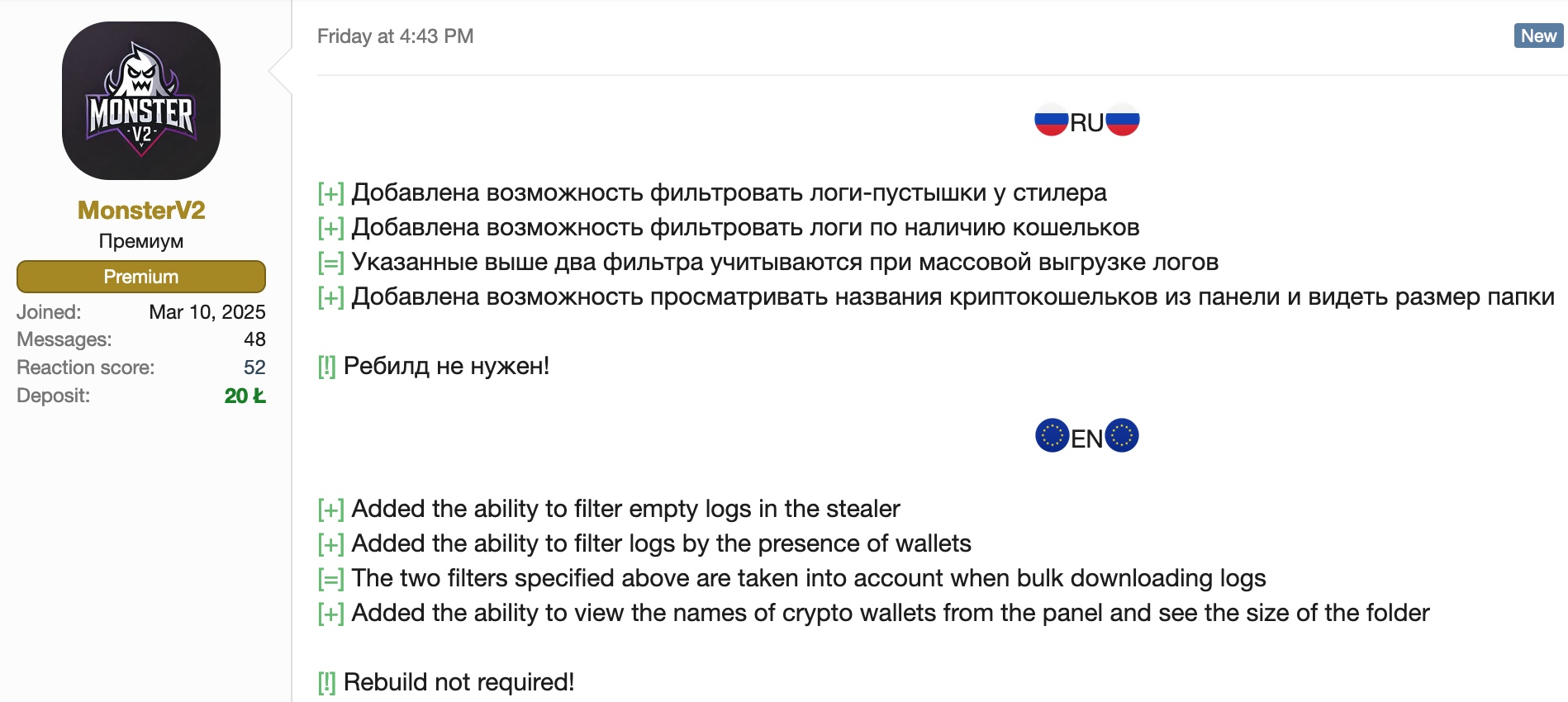
[+] Added the ability to filter empty logs in the stealer
[+] Added the ability to filter logs by the presence of wallets
[=] The two filters specified above are taken into account when bulk downloading logs
[+] Added the ability to view the names of crypto wallets from the panel and see the size of the folder
[!] Rebuild not required!
Screenshot from XSS forum
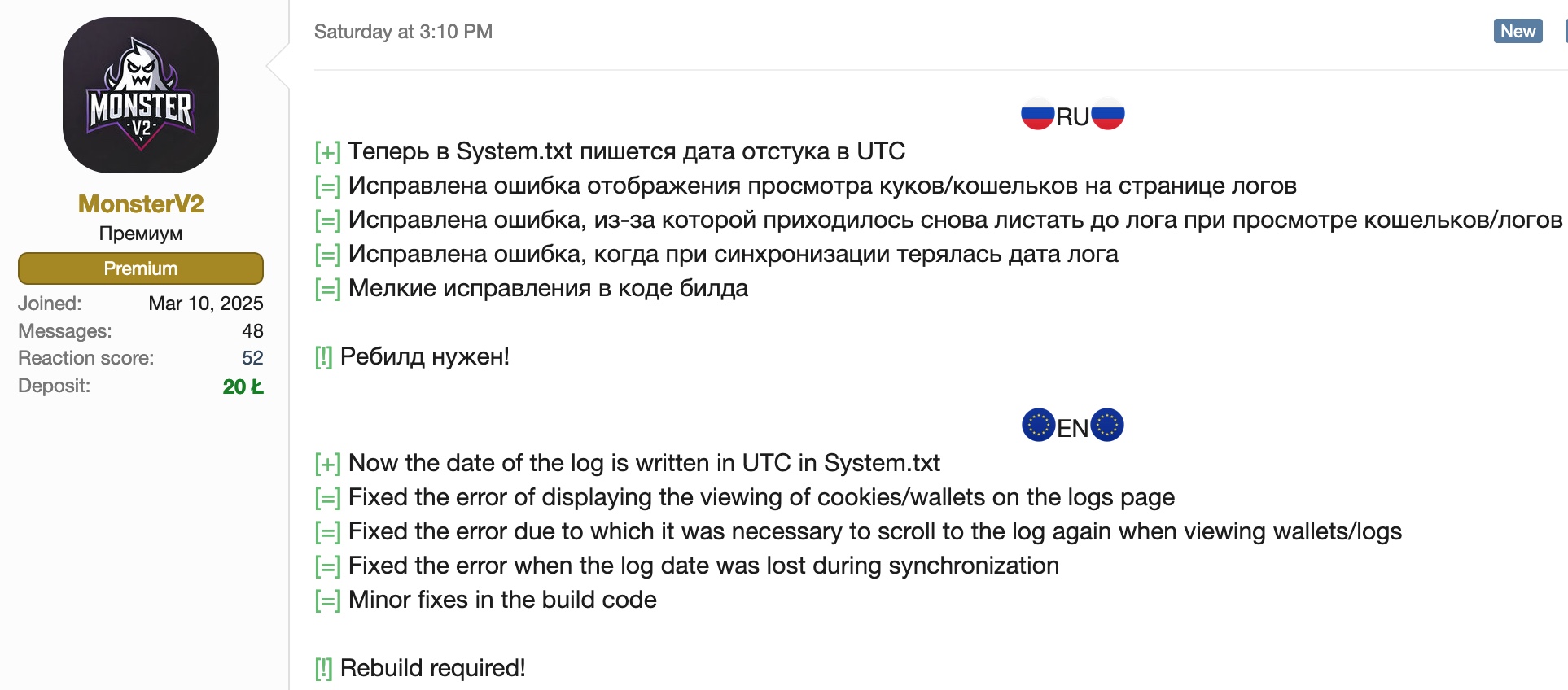
[+] Now the date of the log is written in UTC in System.txt
[=] Fixed the error of displaying the viewing of cookies/wallets on the logs page
[=] Fixed the error due to which it was necessary to scroll to the log again when viewing wallets/logs
[=] Fixed the error when the log date was lost during synchronization
[=] Minor fixes in the build code
[!] Rebuild required!
Screenshot from XSS forum
Mac.c macOS Stealer
Note: The update posts are copy-pasted as is (and machine-translated if post wasn’t available in English, possibly with some minor edits by me)
Comment: It is interesting that the user behind the mac.c stealer first posts about the updates and at the same time puts up the source code for sale.
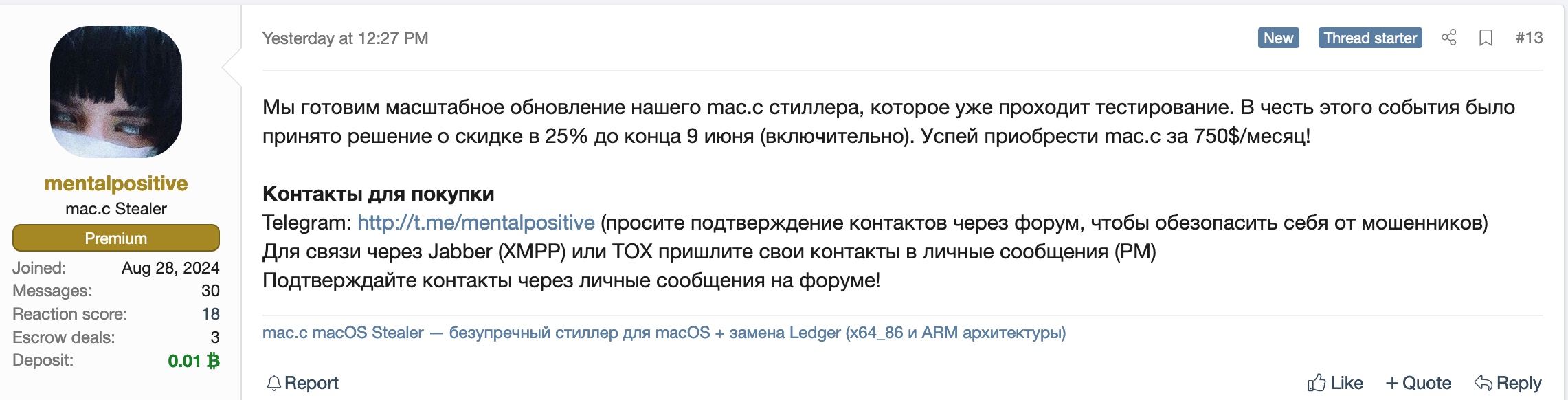
We are preparing a major update to our mac.c stealer, which is already being tested. In honor of this event, we have decided to offer a 25% discount until the end of June 9 (inclusive). Be sure to purchase mac.c for $750/month!
Screenshot from XSS forum
Ready project/business – Source code mac.c Stealer – Stealer for macOS – ARM and x64_86 – ONE TIME SALE
Price: 30.000$+
Hello, dear visitors. I decided to sell the project mac.c Stealer because of lack of time and money for its realization to one buyer only.
A little bit about mac. c
MaaS format stealer for macOS, which works on all architectures – ARM (Silicon) and x64_86 (Intel)
Build is written in C and weighs ~86kb, works on all OS versions above macOS Sierra (Sierra included)
The panel is written in pure PHP, and the log decryption module in Python
Common panel for all users, which allows you to sell subscriptions to the stealer and keep your own project for rent
At the moment the project has 5 active users who renew subscriptions and use the project (ready base of buyers)
The project can be sold both for personal use (or for your team) and for rent (a kind of ready-made business)
Sales topic – https[: //]xssforumv3isucukbxhdhdhwz67hoa5e2voakcfkuieq4ch257vsburuid[.] onion/threads/134505/.
What you get after purchase
Source code of the panel (PHP), builder (Python), log decryption module (Python) and build (C)
Fully customized and ready to sell project on YOUR servers*
Please note that fake ledger replacement module is NOT included in the kit.
Stealer functionality
Collect passwords, cookies, history and autofills of Chromium-based browsers
Collect desktop cryptocurrencies and browser cryptocurrencies
Collect and decrypt keychain with logging
Collect all information about the device, as well as connected devices
Collect Telegram messenger session (in the usual format)
Recursive collection of files from desktop and documents (customizable extensions)
Ability to specify text in modal window at startup
Ability to enable and specify fake error after sending log
Collect authentication tokens from Google Chrome browser (recovery tokens)
What is needed to install the project
Server on Ubuntu for the panel
MacOS server on ARM processor for builder
Cost – waiting for offers**
- – the project will be installed by me personally on your servers
** – the sale will be done through a guarantor (escrow only)
Screenshot from XSS forum
Marketplace Updates
This section provides some numbers taken from the marketplaces, which include numbers of victims based on stealers, top 5 countries, and the victim numbers in the countries of the Nordic region.
RussianMarket
Stealers by number of victims
| Stealer name | Number of victims |
|---|---|
| Lumma | 9,017,053 |
| RisePro | 1,429,242 |
| Vidar | 1,374,054 |
| StealC | 1,018,192 |
| RedLine | 789,487 |
| Raccoon | 329,454 |
| Acreed | 191,569 |
| Rhadamanthys | 24,435 |
Top 5 countries by number of victims
| Country | Number of victims |
|---|---|
| India | 1,472,649 |
| Brazil | 1,104,542 |
| Indonesia | 764,284 |
| Egypt | 699,689 |
| Pakistan | 687,949 |
Nordic region countries
| Country | Number of victims |
|---|---|
| Sweden | 23,921 |
| Denmark | 12,727 |
| Norway | 10,062 |
| Finland | 8,465 |
| Iceland | 1,211 |
| Greenland | 182 |
| Faroe | 117 |
| Åland | 20 |
ExodusMarket
Stealers by number of victims
| Stealer name | Number of victims |
|---|---|
| Lumma | 427,251 |
| RedLine | 34,970 |
| Unknown | 13,628 |
| Rhadamanthys | 12,215 |
| StealC | 5,932 |
| Vidar | 955 |
Top 5 countries by number of victims
| Country | Number of victims |
|---|---|
| India | 52,757 |
| Brazil | 37,499 |
| Indonesia | 30,463 |
| Philippines | 19,318 |
| Egypt | 17,157 |
Nordic region countries
| Country | Number of victims |
|---|---|
| Sweden | 1,224 |
| Denmark | 693 |
| Norway | 528 |
| Finland | 403 |
| Iceland | 66 |
Articles/News
AMOS Variant Distributed Via Clickfix In Spectrum-Themed Dynamic Delivery Campaign By Russian Speaking Hackers
- https://www.cloudsek.com/blog/amos-variant-distributed-via-clickfix-in-spectrum-themed-dynamic-delivery-campaign-by-russian-speaking-hackers
Infostealers Crash Course: A Tradecraft Tuesday Recap
- https://www.huntress.com/blog/infostealers-crash-course-tradecraft-tuesday-recap
The Infostealer Pipeline: How Russian Market Fuels Credential-Based Attacks
- https://resources.reliaquest.com/image/upload/v1748901700/Threat_Report_-_Russian_Market_uqvjq6.pdf
US offers $10M for tips on state hackers tied to RedLine malware
- https://www.bleepingcomputer.com/news/security/us-offers-10m-for-tips-on-state-hackers-tied-to-redline-malware/