A brief look at all things infostealers for the week 21, 2025 (19.05.2025–25.05.2025). This week observed updates…booy, oh boy! What a crazy week! Main news being that Lumma stealer got disrupted. Grabbed some numbers from marketplaces (Exodus Market was offline during the weekend) and some interesting news/articles.
Infostealer Updates
LummaC2
A global operation has disrupted the Lumma Stealer. Folks over at XSS forum were not impressed by the operator of Lumma stealer on how they handled communication and the whole business. Probably, we’ll see resurfacing of Lumma with different branding, or as a private stealer, not in a MAAS form. Time will show, but nevertheless, huge news.
Mac.c macOS Stealer
Note: The update posts are copy-pasted as is (and machine-translated if post wasn’t available in English, possibly with some minor edits by me)
Tested on the latest system versions and fixed some inconsistencies with the latest macOS version. We support working on all system versions starting from macOS Sierra (>10.12.6). Also, communication with clients is now preferably via Telegram, but communication via Jabber or Tox is still possible, please ask for contacts in private forum messages.
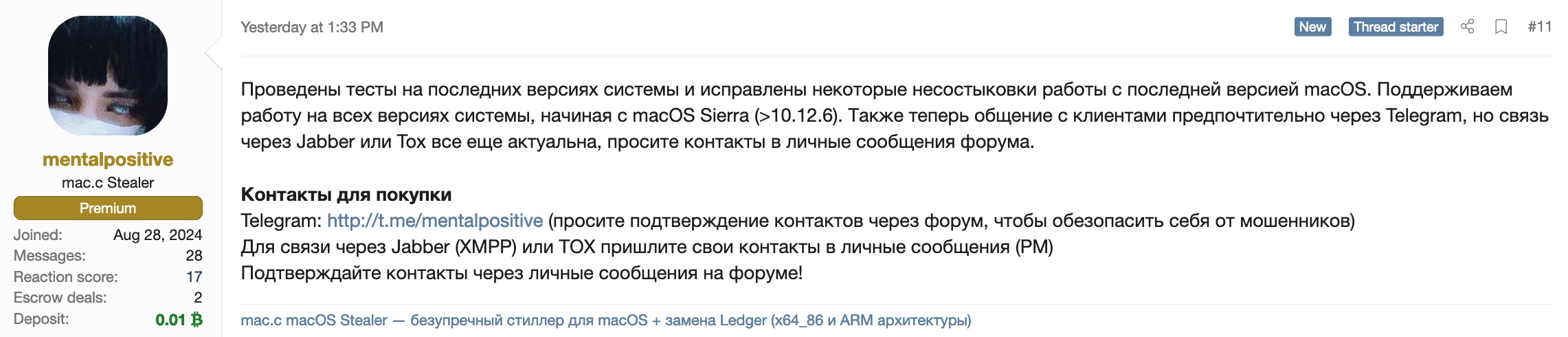
Screenshot from XSS forum
Source Code of Stealer for Linux on Sale
Note: The update posts are copy-pasted as is (and machine-translated if post wasn’t available in English, possibly with some minor edits by me)
Price: 1000
Contacts: Forum PM
I sell the source code of my project – Stealer for Linux
Written in c++, compiled into executable file (ELF 64-bit for x86-64), runs in two clicks.
Collection
- Chromium browsers: Chrome, Opera, Edge, Brave (passwords, cookies, auto-entry, history, more than 60 crypto-extensions).
- Gecko browsers: Firefox, Waterfox (password files, cookies, auto-entry, Metamask extension).
- Telegram tdata.
Build weight up to 1.5 mb.
Stealer doesn’t write anything to disk, collects the archive in memory and sends it to telegram.
All strings are encrypted.
0/61 detections on VirusTotal.
Deal only through the forum guarantor, contact me in a PM.
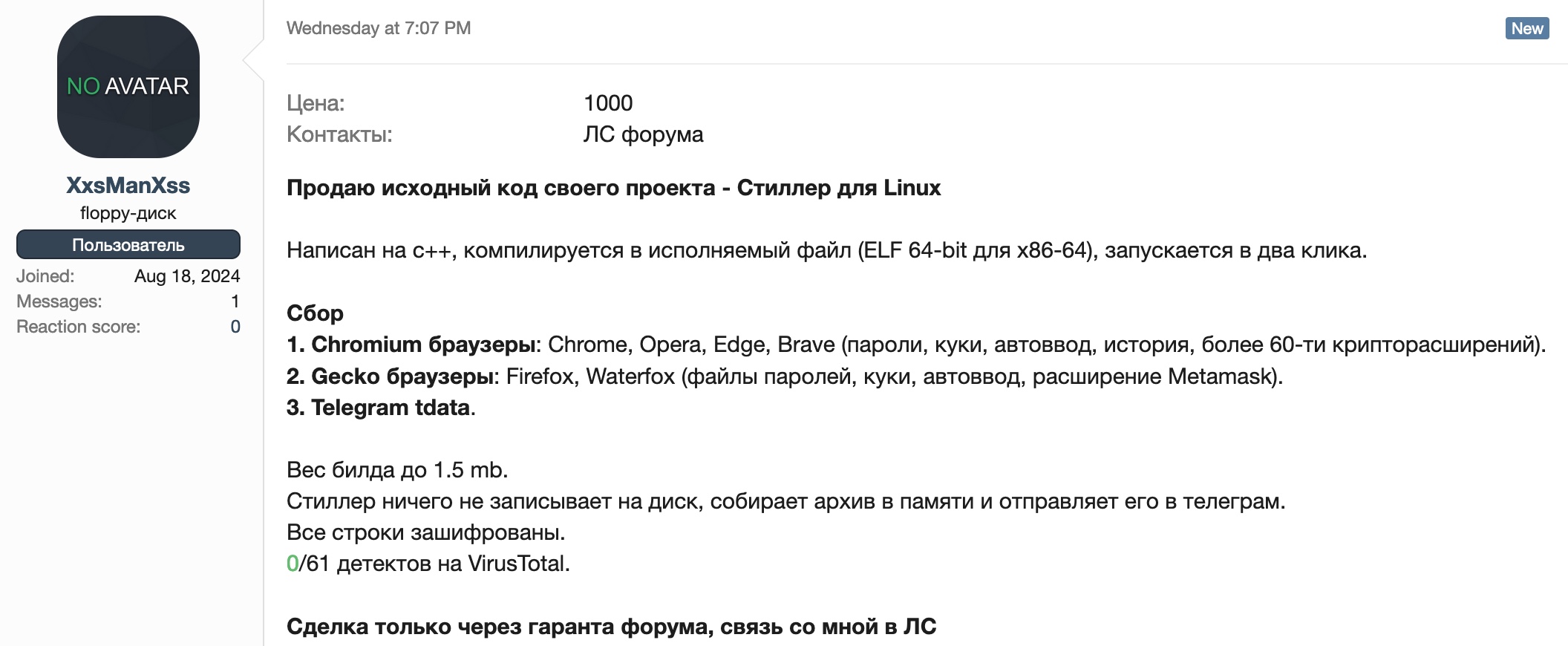
Screenshot from XSS forum
Marketplace Updates
This section provides some numbers taken from the marketplaces, which include numbers of victims based on stealers, top 5 countries, and the victim numbers in the countries of the Nordic region.
RussianMarket
Stealers by number of victims
| Stealer name | Number of victims |
|---|---|
| Lumma | 8,896,960 |
| RisePro | 1,429,326 |
| Vidar | 1,368,088 |
| StealC | 1,010,700 |
| RedLine | 789,589 |
| Raccoon | 329,581 |
| Acreed | 123,330 |
| Rhadamanthys | 24,451 |
Top 5 countries by number of victims
| Country | Number of victims |
|---|---|
| India | 1,443,354 |
| Brazil | 1,093,197 |
| Indonesia | 753,946 |
| Egypt | 691,111 |
| Pakistan | 681,685 |
Nordic region countries
| Country | Number of victims |
|---|---|
| Sweden | 23,552 |
| Denmark | 12,512 |
| Norway | 9,858 |
| Finland | 8,311 |
| Iceland | 1,191 |
| Greenland | 178 |
| Faroe | 116 |
| Åland | 20 |
ExodusMarket
Stealers by number of victims
| Stealer name | Number of victims |
|---|---|
| Lumma | 347,116 |
| RedLine | 34,980 |
| Unknown | 13,629 |
| StealC | 5,948 |
| Vidar | 932 |
Top 5 countries by number of victims
| Country | Number of victims |
|---|---|
| India | 43,332 |
| Brazil | 31,417 |
| Indonesia | 24,275 |
| Philippines | 17,311 |
| USA | 15,392 |
Nordic region countries
| Country | Number of victims |
|---|---|
| Sweden | 962 |
| Denmark | 544 |
| Norway | 427 |
| Finland | 349 |
| Iceland | 61 |
Articles/News
TikTok Videos Promise Pirated Apps, Deliver Vidar and StealC Infostealers Instead
- https://www.trendmicro.com/en_us/research/25/e/tiktok-videos-infostealers.html
Dissecting the macOS ‘AppleProcessHub’ Stealer: Technical Analysis of a Multi-Stage Attack
- https://www.kandji.io/blog/macos-appleprocesshub-stealer
Fake CAPTCHA Attacks Deploy Infostealers and RATs in a Multistage Payload Chain
- https://www.trendmicro.com/en_us/research/25/e/unmasking-fake-captcha-cases.html
Lumma Stealer: Breaking down the delivery techniques and capabilities of a prolific infostealer
- https://www.microsoft.com/en-us/security/blog/2025/05/21/lumma-stealer-breaking-down-the-delivery-techniques-and-capabilities-of-a-prolific-infostealer/
The Sting of Fake Kling: Facebook Malvertising Lures Victims to Fake AI Generation Website
- https://research.checkpoint.com/2025/impersonated-kling-ai-site-installs-malware/
Caught in the CAPTCHA: How ClickFix is Weaponizing Verification Fatigue to Deliver RATs & Infostealers
- https://www.sentinelone.com/blog/how-clickfix-is-weaponizing-verification-fatigue-to-deliver-rats-infostealers/
De-obfuscating ALCATRAZ
- https://www.elastic.co/security-labs/deobfuscating-alcatraz
Suspected Russian Threat Actors Leverage Tigris, Oracle Cloud Infrastructure, and Scaleway to Target Privileged Users with Lumma Stealer
- https://www.catonetworks.com/blog/cato-ctrl-suspected-russian-threat-actors/
ESET takes part in global operation to disrupt Lumma Stealer
- https://www.welivesecurity.com/en/eset-research/eset-takes-part-global-operation-disrupt-lumma-stealer/#iocs
Lumma infostealer infected about 10 million systems before global disruption
- https://cyberscoop.com/lumma-infostealer-widespread-victims/
Threat Actors Deploy LummaC2 Malware to Exfiltrate Sensitive Data from Organizations
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-141b
Cloudflare participates in global operation to disrupt Lumma Stealer
- https://www.cloudflare.com/en-gb/threat-intelligence/research/report/cloudflare-participates-in-joint-operation-to-disrupt-lumma-stealer/
Katz Stealer Threat Analysis
- https://www.nextron-systems.com/2025/05/23/katz-stealer-threat-analysis/